Ukraine: Analysis of the new disk-wiping malware (HermeticWiper)
By Cluster25 Threat Intel Team
February 24, 2022
Very recently a new type of destructive malware named by the security community “HermeticWiper” was used to attack organizations and entities in Ukraine shortly before Russia began military operations against the same country. HermeticWiper is an executable file signed with a likely stolen certificate issued to Hermetica Digital Ltd. It has been reported by researchers at ESET on 2022/02/23
Insights
We analyzed the file identified by the following SHA256 hash : 1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591On the basis of some evidences extracted from the analyzed samples, it is possible to hypothesize that the preparation and the development phases of this piece of malware (and may be the military operation that soon followed its spread) had been going on for some months already.
Technically speaking the first actions carried out when executed are aimed at opening its current process using the GetCurrentProcess API and at accessing the token with the OpenProcessToken.
Immediately after it adjusts the token privileges using the AdjustTokenPrivileges to add the SeShutdownPrivilege and SeBackupPrivilege.
It proceeds by dynamically resolving Wow64DisableWow64FsRedirection, Wow64RevertWow64FsRedirection, IsWow64Process from kernel32.dll library using the GetModuleHandle and the GetProcAddress API’s.
OS version is verified through IsWow64Process and VerifyVersionInfoW API’s. Based on the OS version load 1 of the 4 resources as shown following:
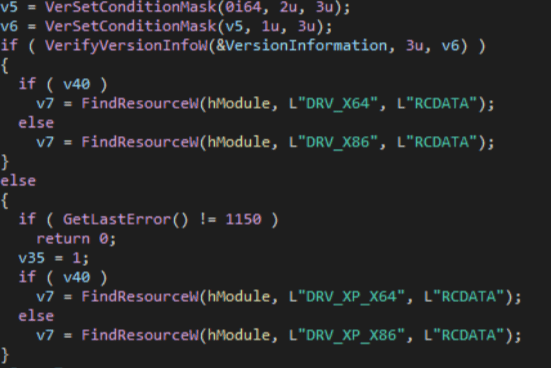
The resources contain ms-compressed copies of the empntdrv.sys from EaseUS driver suite used in the next subroutines to access physical drives and getting partition information.
This adds an obfuscation layer to the current wiper since a lot of functionality are accessed through the DeviceIoControl API (calling the specific IOCTLs).
After that, the resource is loaded and decompressed. Next, the
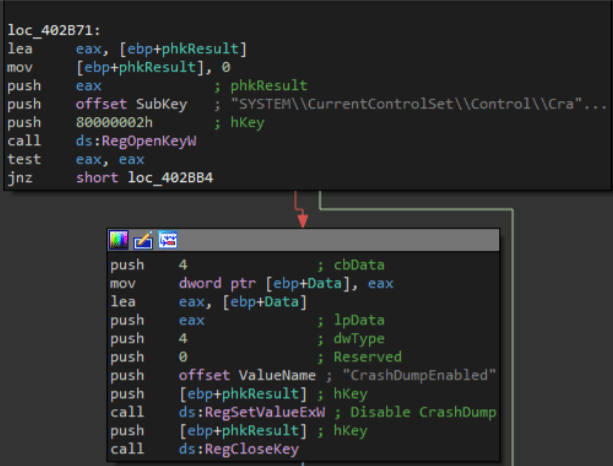
SYSTEMCurrentControlSetControlCrashControl
registry key is opened to disable the CrashDump feature (enabled by default in Windows).
In particular, the DWORD CrashDumpEnabled value is changed from 1 to 0.
directory (the filename is computed at runtime using randomness).
To ensure the driver execution the process token is modified again to add the SeLoadDriverPrivilege permission and a new service is created using the CreateServiceW API.
Instead, if the service already exists, the ChangeServiceConfigW API is used to force the execution of the service with the SERVICE_DEMAND_START flag. Finally, the StartServiceW API is used to start the service pointing to the utility driver.
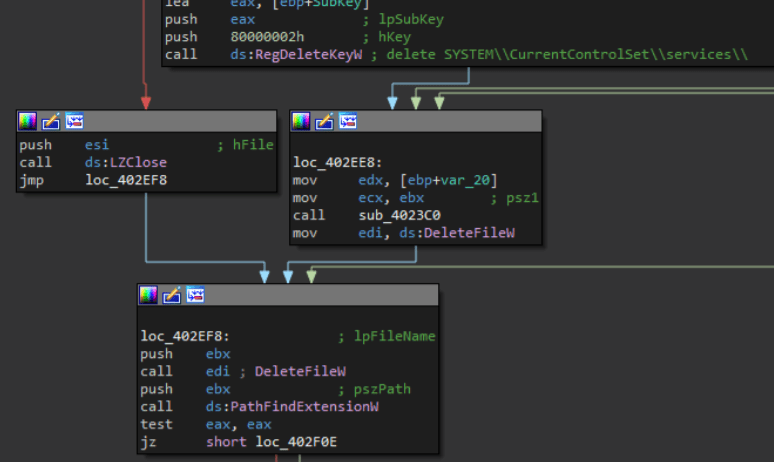
After some sleep, the reg key
SYSTEM\CurrentControlSet\services\
and the driver file stored on the filesystem are deleted
Subsequently, the vss service (shadow copies service) is opened and the ChangeServiceConfigW API is used to set the flags SERVICE_DISABLED and SERVICE_CONTROL_STOP.
Afterwards, the system physical drivers are enumerated multiple times with a counter from 1 to 100.
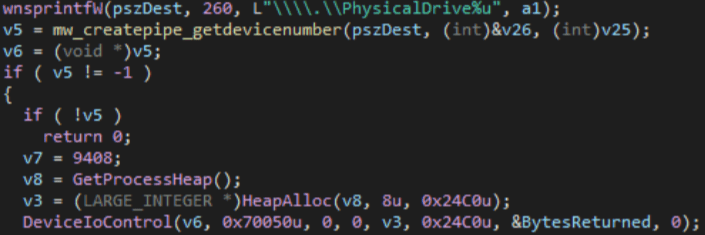
For each found physical drive, the \.EPMNTDRV is called with the appropriate device number using the DeviceIoControl API.
Then, for each driver found, the malware starts a bit swapping routine to corrupt the Master Boot Record (MBR) for every physical drive.
The corruption is a little different between FAT and NTFS partitions.
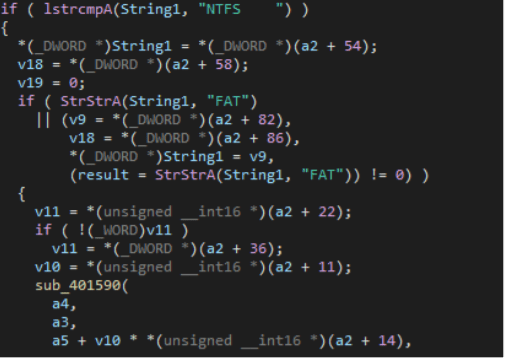
For the NTFS partitions, the malware parses the Master File Table (MFT) before calling the bit swapping routine.
The bit swapping routine is supported with the usage of cryptographic context API’s (like CryptoAcquireContext), the generation of random bytes to corrupt the partition and the usage of DeviceIoControl with the just-created service to access the physical drives.
Further functionality refers also to the encryption of specific MFT fields ($bitmap and $logfile) or NTFS streams like $DATA, $I30 or $INDEX_ALLOCATION with some references to “ntuser”.
After the corruption subroutines, the malware enumerates also common folders but currently still not totally clear why as the wiping activities are already been operated. Anyway, the folder are the following:
1. My Documents 2. Desktop 3. AppData 4. Windows Event Logs (C:\Windows\System32winevt\Logs)At the end this piece of malware waits for different sleeping treads and initialize a system shutdown destroying the victim system.
Conclusions
HermeticWiper is a new type of destructive malware, significantly different from WhisperGate, the previous wiper used against targets in Ukraine. Destructive attacks perpetrated through pieces of malware of this type are focused on making essential services and critical infrastructures unavailable.
In this case, HermeticWiper probably works in support of Russian military operations.